The ultimate device deployment guide for distributed teams
Hiring team members in different countries is great for bringing diverse ideas and innovation to the business, but it also adds a layer of complexity to IT operations. From procuring hardware and setting those mobile devices up with company settings to delivering the equipment on time for employees to use it, there are many things to get right when it comes to remote IT onboarding.
A study by software company Talmundo found that it took 43% of surveyed employees more than a week to get basic workstation logistics and tools. And 40% did not get the minimum required to start their new job. Mobile device deployment timeliness can impact the onboarding experience for new hires and their productivity.
Conversely, proper mobile device retrieval is crucial to keep corporate-owned data safe when employees leave. According to research commissioned by Oomnitza, 49% of companies lost at least 5% of corporate-issued assets during offboarding. Meanwhile, 42% of organizations reported at least 5% instances of unauthorized access to company resources after an employee left.
New device deployment models streamline this task and make it easy for distributed companies to onboard many devices and set up employees efficiently. In this blog post, we will discuss device deployment, the proper device deployment process for distributed teams, the best practices to help global businesses ace this task, and modern solutions that can streamline your mobile device program. Let’s dive in!
What is device deployment?

Device deployment is the process of provisioning and configuring hardware and software on devices to ensure they are fully prepared and optimized for use within a company's IT environment. At its core, device deployment brings devices into practical action, delivering them to the right people at the right time and with the correct apps, settings, and configurations, allowing employees to work efficiently.
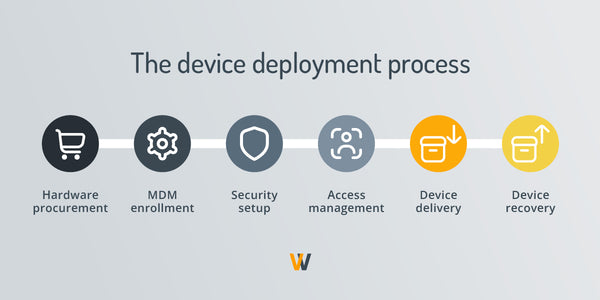
Deploying a device means systematically preparing and distributing technology—such as laptops, smartphones, and tablets—to employees, ensuring that each piece of equipment is ready for immediate use. A robust mobile device program considers a few key steps that include hardware procurement, security setup, device delivery and the retrieval of that equipment.
Deployment models can vary from Bring Your Own Device (BYOD) services to corporate-owned deployment strategies. While BYOD can be a suitable deployment model for small businesses, it is preferable for them to transition to a more secure and centrally managed deployment model, such as the company-owned model, as they expand and mature.
BYOD environments allow employees to use a personal device for work-related purposes. This way, each employee uses their own device to access company resources and data. While the model eliminates the need for device procurement, it heightens business security risks. Without virtual desktop infrastructure, BYOD environments are prone to data breaches and cybersecurity threats.
What does the device deployment process look like?
Device deployment is closely tied to hiring. When a new hire comes into the organization, companies must ensure they have their own device, a laptop or desktop computer with all the company settings, permissions based on that employee’s role, and access to relevant business data. In distributed environments, the added step includes shipping that equipment to the employee’s location, anywhere on the map.
Once IT infrastructure was designed for a centralized office environment, but having corporate owned personally enabled devices now allows the shift to distributed environments where businesses can ensure a safe digital ecosystem.
Deployment involves multiple steps, from the initial procurement of hardware to the eventual recovery of devices at the end of their lifecycle. Here’s a detailed breakdown of what device deployment looks like for distributed teams:
Hardware procurement
The journey begins with hardware procurement, a critical phase where organizations select and acquire the necessary devices, such as laptops, desktops, or mobile phones. This step requires careful consideration of the company's specific needs, budget constraints, compliance requirements, and the tech needs of its workforce. It's not merely about choosing the right type of device but also planning for its purchase in the amounts needed to support current employees and future growth. The goal is to secure hardware that meets the operational demands and aligns with the organization's IT standards and security protocols.
Device enrollment into an MDM solution
Once the devices are procured, the next step involves their enrollment into an MDM solution. Mobile device management software is pivotal in deployment, allowing IT admins to manage, monitor, and secure the organization’s mobile devices from a centralized platform regardless of operating systems. This includes deploying corporate policies and configurations and ensuring devices comply with the company's IT security requirements and standards. MDM solutions facilitate over-the-air (OTA) enrollment, which is excellent for deploying mobile devices to distributed teams, enabling seamless setup and integration into the company's IT ecosystem.
Configuring company security settings
Configuring the security settings of each device is a vital stage in safeguarding corporate data and resources. This involves installing security software, configuring firewalls, enabling data encryption, and setting up VPN access for secure remote connections. The objective is to create a robust security framework that protects corporate information against threats while ensuring that devices remain functional and accessible for user needs. This balance is crucial in maintaining productivity without compromising on security.
Creating accounts, allotting privileges, and access rights
An integral part of deployment is the creation of user accounts and allocating appropriate privileges and access rights. This step ensures that employees have access to the necessary applications, data, and resources relevant to their roles. It's about establishing a secure and efficient environment where users can perform their duties effectively. Proper access rights and privileges management also plays a critical role in minimizing potential internal and external security risks.
Delivering the ready-to-use device to the employee
This phase is critical in ensuring employees have everything to start working immediately, including access to corporate networks, applications, and data. This step involves logistical considerations for distributed teams, such as secure shipping and handling, to ensure that devices reach their destinations safely and on time.
Recovering the device at the end of lifecycle
Device deployment also encompasses end-of-lifecycle management, which involves device recovery, repurposing, or disposal. Effective lifecycle management ensures that devices are protected and either efficiently redeployed within the organization, securely wiped of all data before disposal, or recycled in an environmentally and cost-responsible manner. This stage is essential for maintaining IT asset security and compliance and managing the organization's technological footprint responsibly.
What are the challenges of IT onboarding for distributed teams?

The global nature of today's workforce exacerbates the unique challenges regarding IT onboarding for distributed teams. Companies worldwide know from experience that device deployment can be harsh on their IT teams.
At GroWrk, we have seen different perspectives on these challenges. On one side, Canadian company Orium tried building relationships with Latin American vendors to procure their own devices and provisioning equipment for new hires joining their company in those countries.
Meanwhile, Typeform would have to send their IT team to co-working spaces to prepare and ship devices to their distributed team members. In both cases, these in-house solutions were resource-intensive and not scalable.
Managing international logistics, coordinating with vendors across different regions, and ensuring the secure storage and shipping of devices are three main hurdles distributed teams must deal with daily in their IT operations. Let’s look at each of these challenges in more detail:
Global logistics
Managing global logistics is one of the major challenges in IT onboarding for distributed teams. Ensuring that the right equipment reaches the right employee at the right time, regardless of location, can be a head-scratcher.
This challenge is not just about timing; it involves navigating customs regulations, dealing with import taxes, and ensuring compliance with local laws—all of which can vary significantly from one country to another.
The logistics become even more daunting when considering the need to scale operations across multiple countries simultaneously, each with its own rules and regulations.
Managing vendors worldwide
Another critical aspect is the management of vendors across countries. Organizations must establish relationships with reliable suppliers and service providers in different regions to ensure employees can access the necessary equipment and support.
This requires a deep understanding of the local market, including which vendors offer the best value, reliability, and service quality. It also involves negotiating contracts, managing orders, and ensuring timely delivery—all while maintaining consistent standards across all locations.
The complexity increases with the need for specialized equipment or software, which may not be readily available in certain regions, requiring further coordination and planning.
Storage and shipping
Storage and shipping represent additional logistical challenges, particularly when pre-configuring devices with the necessary software and settings before delivery to remote employees.
Organizations need secure storage facilities to house inventory before deployment, which can be costly and require significant management oversight, especially when operating globally. The shipping process adds another layer of complexity, ensuring that devices are packed securely, shipped efficiently, and tracked accurately to avoid losses or delays.
Moreover, the risk of tampered devices during transit or storage requires robust security measures to protect sensitive company data pre-loaded on these devices.
Best practices for device deployment for distributed teams

For distributed teams, effective device deployment is crucial for maintaining productivity, security, and operational efficiency. Implementing best practices in device deployment can significantly streamline operations and enhance the remote work experience. Here are some key strategies to ensure success:
Plan procurement in advance
Advanced planning for device procurement is essential to navigate the challenges of supply chain disruptions and ensure that the necessary equipment is available when needed. This involves forecasting future needs based on projected team growth and potential technology updates.
Organizations can avoid delays in employee onboarding and productivity losses by understanding the lead times for different devices and anticipating the needs of new hires or technology refresh cycles. Establishing relationships with multiple suppliers can also provide alternatives in case of stock shortages or delays.
Secure storage and shipping
The logistical aspect of storing and shipping devices securely to distributed team members across the globe cannot be understated. Secure storage ensures that devices are kept in a safe environment, protecting them from damage or unauthorized access before deployment.
Choosing reliable logistics partners who can provide tracking and insurance is crucial for shipping. Implementing robust packaging solutions to protect the devices during transit and ensuring that shipping practices meet security standards will mitigate risks of damage, loss, or stolen devices.
Enroll devices in MDM
Enrolling existing and new devices in an MDM solution is a cornerstone of effective mobile device deployment. Mobile device management features allow IT administrators to manage and secure mobile devices remotely throughout their lifecycle. This includes installing necessary applications, configuring settings to comply with company policies, applying security measures, and even wiping devices remotely if they are lost or stolen.
MDM solutions facilitate the deployment of devices to distributed teams by ensuring that all devices are consistent in terms of software, security policies and settings, and access controls, regardless of their physical location.
Manage user access and identity
Managing user access and identity efficiently is vital to safeguarding company data and ensuring employees can access the resources they need to work effectively. This involves setting up user accounts, defining roles, and assigning access rights based on those roles.
Identity and Access Management (IAM) systems can automate this process, providing a secure and efficient way to manage user identities and access permissions across all company resources.
Implementing Role-Based Access Control (RBAC) ensures that employees only have access to the information and tools necessary for their specific job functions, minimizing the risk of internal and external threats.
Automating device deployment with GroWrk
Automating deployment is essential for companies with distributed teams, ensuring employees have the necessary tools and resources regardless of location. GroWrk offers a comprehensive solution to streamline and automate these processes, leveraging advanced technology and a global network. Here’s how GroWrk's features facilitate this automation:
User-friendly dashboard
GroWrk's platform is centered around a user-friendly dashboard that simplifies the management of IT assets. It allows companies to easily select the make and model of mobile devices for their employees, tailor configurations to meet specific job roles, and track the deployment process from procurement to delivery. This dashboard provides IT managers with complete visibility into the status of each device, enabling them to make informed decisions and adjustments as needed, all from a single interface.
Integrations with HRIS systems
By integrating directly with Human Resources Information Systems (HRIS), GroWrk automates the onboarding process for new hires by initiating the device deployment sequence as soon as an employee is added to the HR system. This seamless integration ensures that new team members have their required IT equipment by their start date, significantly reducing the administrative burden on IT and HR departments and eliminating manual entry errors.
MDM enrollment
GroWrk simplifies the enrollment of devices into MDM solutions. This feature ensures that all deployed devices are secured, configured, and compliant with the company's requirements and policies before they reach the employee. MDM enrollment through GroWrk allows for over-the-air (OTA) setup and configuration, meaning devices can be fully prepared for use when they arrive at the employee’s location. This capability is crucial for maintaining security standards and operational efficiency across distributed teams.
Worldwide coverage
One of GroWrk's standout features is its global logistics network, enabling users to manage and automate IT equipment shipping and delivery to over 150 countries. This extensive coverage ensures that organizations can support their distributed workforce virtually anywhere in the world. GroWrk handles all aspects of logistics, ensuring that devices and services are delivered safely and on time.
By leveraging GroWrk’s solution, companies can automate much of deployment, from selection and configuration to shipping and delivery. This automation saves time, reduces costs, and ensures that distributed teams have the tools to be productive and secure.
GroWrk's platform represents a significant advancement in managing distributed teams, providing a scalable, efficient solution to one of the most pressing challenges facing global companies today. Schedule a demo to learn more about GroWrk’s capabilities.
Mara Quintanilla
February 23
